Get `clientId` and `clientSecret`
(source)
You’ll need credentials:
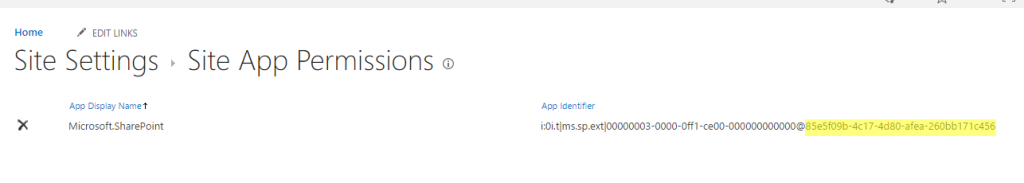
`clientId`– required string, client id obtained when registering the addin`clientSecret`– required string, client secret obtained when registering the addin`realm`– your SharePoint Online tenant id. The easiest way to find tenant is to open SharePoint Online site collection, click Site Settings → Site App Permissions. Under this page you wll see at least one app “Microsoft.SharePoint”. The tenant id (realm) is highlighted in the image below:
Example of the expected result:
{
clientId: '28bq7e56-8c3a-487d-hbfb-ef1a74539cbe',
clientSecret: 's6LZ4VvoeKOS+MyAhklcavsyJBF4XhWo06OgY6czYJ0=',
realm: '85e5f09b-4c17-4d80-afea-260bb171c456'
}
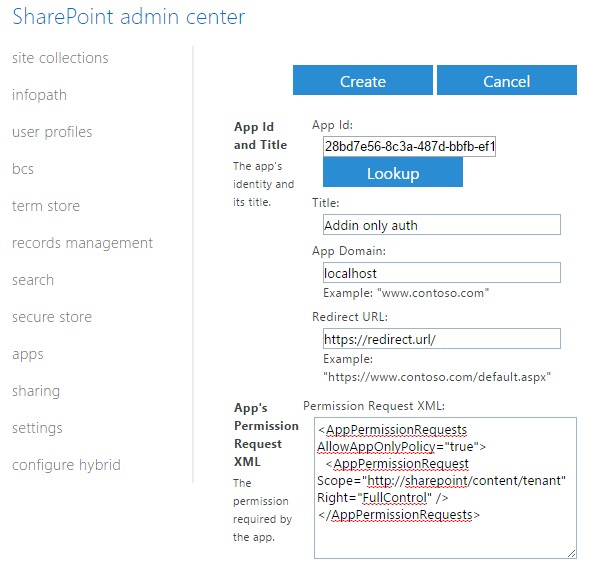
To get the credentials, you need to register a new addin inside SharePoint Online, by fellowing these steps:
- Open SharePoint Online app registration page, e.g.
https://contoso.sharepoint.com/sites/dev/_layouts/15/appregnew.aspx - Click on “Generate” for Client id and Client Secret, fill in Title, App Domain, Redirect URI (you can type in any values you want)
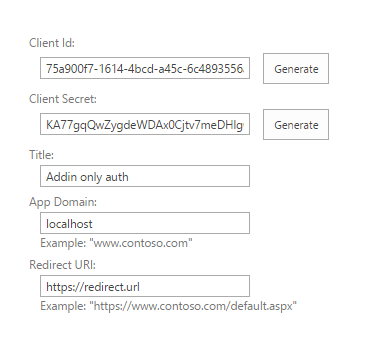
- Click on “Create” and save generated Client Id and Client Secret
- [IF YOU HAVE TENANT RIGHTS] Now you need to apply permissions to the newly registered app. If you want to register the app once and use it for any site collection, it’s better to apply tenant scope permissions, so you can use the credentials everywhere inside your SharePoint tenant. To apply tenant scoped permissions, open
AppInv.aspxpage under SharePoint adminstration web site, e.g.https://[YOUR_ORGANIZATION]-admin.sharepoint.com/_layouts/15/appinv.aspx, copy paste Client Id from step n°3 into App Id field and click “Lookup”. - [IF YOU HAVE TENANT RIGHTS] You will see your registered app, paste in the following XML into the “Permission Request XML” field and click “Create”:
<AppPermissionRequests AllowAppOnlyPolicy="true"> <AppPermissionRequest Scope="http://sharepoint/content/tenant" Right="FullControl" /> </AppPermissionRequests> - [IF YOU ARE NOT A TENANT] If you only want to give permissions on 1 site collection, you can register the app on a regular site collection by using url
https://contoso.sharepoint.com/sites/dev/_layouts/15/appinv.aspx. In this case you are not able to use tenant scoped permissions and can only apply site collection permissions:<AppPermissionRequests AllowAppOnlyPolicy="true"> <AppPermissionRequest Scope="http://sharepoint/content/sitecollection" Right="FullControl" /> </AppPermissionRequests> - You will see addin “Trust” confirmation, click on “Trust It”:
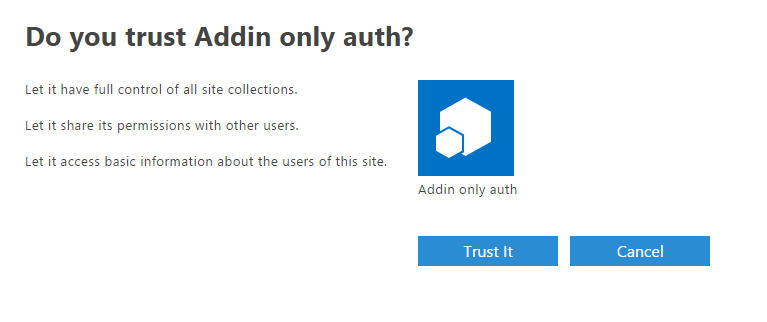
if trust-it button is not enabled and you get a red label saying tenant admin needs to trust the app, go back and try again in a few minutes. - Now you can use client id and client secret to send authenticated http requests.
To know more about the XML permissions, you can check the Microsoft documentation.
Get Access Token
(you can find a C# code as an example)
You need to do a POST request to https://accounts.accesscontrol.windows.net/[YOUR_TENANT_REALM]/tokens/OAuth/2 with a “Content-Type” header that has the value “application/x-www-form-urlencoded”, and the body parameters that must be:
- "grant_type":"client_credentials"
- "client_id":"[YOUR_CLIENT_ID]@[YOUR_TENANT_REALM]"
- "client_secret":"[YOUR_CLIENT_SECRET]"
- "resource":"00000003-0000-0ff1-ce00-000000000000/dell.sharepoint.com@[YOUR_TENANT_REALM]"
See below an example in PHP:
$curl = curl_init(); curl_setopt($curl, CURLOPT_URL, "https://accounts.accesscontrol.windows.net/[YOUR_TENANT_REALM]/tokens/OAuth/2"); curl_setopt($curl, CURLOPT_HTTPHEADER, [ "Content-Type: application/x-www-form-urlencoded" ]); curl_setopt($curl, CURLOPT_POSTFIELDS, http_build_query([ "grant_type" => "client_credentials", "client_id" => "[YOUR_CLIENT_ID]@[YOUR_TENANT_REALM]", "client_secret" => "[YOUR_CLIENT_SECRET]", "resource" => "00000003-0000-0ff1-ce00-000000000000/dell.sharepoint.com@[YOUR_TENANT_REALM]" ])); curl_setopt($curl, CURLOPT_RETURNTRANSFER, true); $response = json_decode(curl_exec($curl)); curl_close($curl); echo $response->access_token;
The response should contain an access token. Example:
{
"token_type":"Bearer",
"expires_in":"86399",
"not_before":"1679393911",
"expires_on":"1679480611",
"resource":"00000003-0000-0ff1-ce00-000000000000/dell.sharepoint.com@[YOUR_TENANT_REALM]",
"access_token":"eyJ0eXAiOiJKV1QiLCJhbGciOiJSU[...]SxXA5Lqbk1OcOVdwQ"
}
Finally, you can do your REST API request to SharePoint Online with passing the header “Authorization” that has the value “Bearer [YOUR_ACCESS_TOKEN]”.